I have successfully enabled IMA (including the dracut module integrity and with an X.509 key for custom policies) and am trying to enable EVM with only X.509 keys (so no symmetric key for EVM HMAC). This process is broadly described here although it doesn’t explain enabling EVM with X.509 keys, and I believe the included documentation for EVM key creation is slightly inaccurate anyway (see the commands I used instead later).
If I try to do this setup without a symmetric key for EVM HMAC, my Fedora system won’t boot, but it will if I do add the symmetric key for EVM HMAC.
Of course I have been updating all the signatures as necessary, using sudo find / -fstype xfs -type f -uid 0 -exec evmctl sign --imasig '{}' -k keys/custom_ima.priv \;
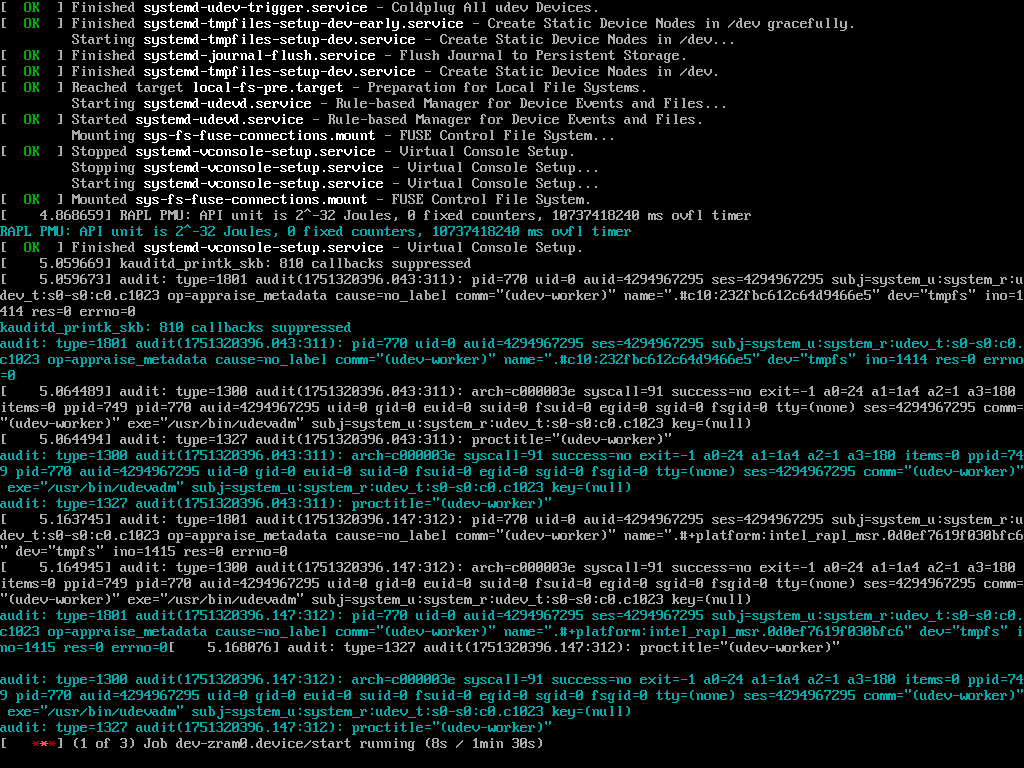
The following screenshots demonstrate where the boot gets stuck at the bottom (although they have been taken on different days after testing different setups, so the context of the rest of the boot logs may not actually be consistent or relevant):
Thus, I figured it was worth at least trying with a symmetric key for HMAC. To set up an HMAC key for EVM, I’ve done the following:
# (logged in as root user)
# Create a TPM SRK
tpm2_createprimary --key-algorithm=rsa2048 --key-context=key.ctxt
tpm2_evictcontrol -c key.ctxt 0x81000001
# Create a kernel masterkey
keyctl add trusted kmk-trusted "new 32 keyhandle=0x81000001" @u
keyctl pipe $(keyctl search @u trusted kmk-trusted) > /etc/keys/kmk-trusted.blob
# Create an EVM HMAC key
keyctl add encrypted evm-key "new trusted:kmk-trusted 64" @u
keyctl pipe $(keyctl search @u encrypted evm-key) > /etc/keys/evm-trusted.blob
Having an HMAC key set up as well as the X.509 key located in /etc/keys/evm/, the system can boot and appears to use both keys successfully.
According to the IMA/EVM documentation, I think it should be possible to run EVM with only the X.509 key, and in fact it is desirable for me in a development environment because this should allow resigning attributes during development testing, while having an HMAC key explicitly disallows this (see here).
Does anyone have any ideas for fixing this? I am happy to provide more details or assist in setting up IMA if necessary (the process is understandably quite brittle).